Cracking OS X Lion Passwords
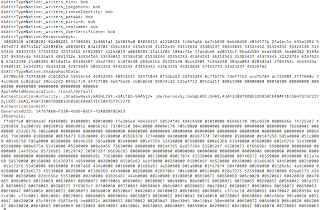
UPDATE [2011-10-15]: The issues described in this post have now been resolved by Apple. Users running OS X Lion 10.7.2 or security update 2011-006 are no longer affected by the vulnerabilities detailed below (CVE-2011-3435 and CVE-2011-3436). For further details on this security update please see Apple's advisory . In 2009 I posted an article on Cracking Mac OS X passwords . Whilst this post has been quite popular, it was written for OS X 10.6 and prior. Since the release of Mac OS X Lion (10.7) in July, I have received numerous requests for an update. Typically, I would have just updated the existing article without the need for a new post. However, during my research I discovered something interesting about OS X Lion that I'd like to share. In previous versions of OS X (10.6, 10.5, 10.4) the process to extract user password hashes has been the same: obtain the user's GeneratedUID and then use that ID to extract hashes from a specific user's shadow file (See my pr...

1337day.com
ReplyDelete1337day.com
ReplyDeleteThis comment has been removed by the author.
Deleteexploit-h.org
ReplyDeletewordsmaker87@gmail.com
ReplyDeletevulnerability-lab.com ;)
ReplyDeletecxsecurity.com CVE and CWE in one place
ReplyDeleteAmazing blog! I really like the way you explained such information about this post with us. And blog is really helpful for us this website
ReplyDeleteThunderSoft GIF Maker Crack
Xmanager Power Suite Crack
CudaText Crack
AnyMP4 Video Converter Crack
Malwarebytes Anti-Exploit Crack
ascrack.org